How to deal with cyber-attacks, increase risk resilience, and act with integrity at once? Not an easy task these days. Read this article to learn more about the GRC framework and get a well-proven five-step action plan for implementing it in your organization.
Enterprise Security and GRC: What Is It And How Does It Work
Imagine that you are a bank CEO. You assume your morning will begin as usual: you will grab a coffee on your way to the office, and the working day will start with a routine mail check.
Instead, it started with tons of notifications from nervous employees that they had lost control over the banking system. What happened? One employee had simply clicked on a link in an email that seemed to be from a trusted sender. This resulted in million-dollar losses.
This short story is about one of the most shocking cybercrimes. Carbanak, a hacking group also known as Cobalt, targeted over 100 financial institutions from 40+ countries and committed more than 100 hacks, stealing over $1.24 billion. The cyber gang created malicious software that controlled bank accounts, money transfers, ATMs, etc.
Unfortunately, it is only one example of cybercrimes that are common now. How can enterprises protect their mission-critical data and prevent security breaches? The following article comprehensively describes companies' situations and provides valuable tips and strategies for enterprise security.
What is Enterprise Cybersecurity?
Broadly speaking, enterprise cybersecurity solutions are designed to prevent Internet attacks. Depending on the industry, a cyberattack can be an act of sabotage, financial larceny, acquisition of information (industrial espionage), or even a political motive. However, the attacks always have one thing in common: they leave a lot of damage.
Malware, system failures, and the deletion or falsification of databases can make day-to-day business difficult or even temporarily impossible. Added to this is the negative reputation an enterprise suffers when attacks become public. Therefore, companies need to protect their internal and customer data – and they need it right now!
Why Enterprises Should Care About Cybersecurity More Than Ever
Leading authorities and industry associations are sounding the alarm: cyber-attacks are constantly growing. The damage caused is already costing companies billions. Still, cyberattackers continually find new ways to access enterprise networks.
The following reasons demonstrate why every company needs a cyber security strategy to counter security risks that are becoming increasingly complex effectively.
1. Digital transformation is under threat
The current developments in Industry 4.0 and IoT are creating more and more opportunities for attack. The worsening threat landscape has tangibly impacted digital transformation projects globally, slowing innovation worldwide. Over half (55%) of Armis study respondents say that their organizations have stalled or stopped digital transformation projects due to these threats. This percentage is even higher in specific countries, including Australia (79%), the USA (67%), Singapore (63%), the UK (57%), and Denmark (56%).
While many digital transformation initiatives have resulted in new sources of revenue and greater profits, security collaboration has yet to catch up.
2. Cloud vulnerability
A cloud data protection incident can be costly and damage a brand's reputation permanently. Whether a company is at fault or not, a data breach caused by cloud security vulnerabilities costs companies an average of $4.8 million. The Thales survey highlights that the most significant risks in cloud operations are infrastructure compromise (67%) and third-party risk (50%). The threats include malware, ransomware, and phishing attacks.
3. Business sustainability
Today's IT is characterized by extensive networking. It no longer only affects particular areas in a company, such as administration. Instead, IT systems are integrated into every department through cloud services or communication tools.
As a result, a failure in one sub-area will often affect other departments, if not shut them down. Such absences from work have far-reaching financial consequences and may damage a company's reputation if deadlines are not met or the company cannot fulfill orders.
Regardless of the industry or the company's size, most businesses have individual measures for implementing cybersecurity solutions. But how can companies foresee potential threats? SAP has developed a tailor-made solution to address continually created security-related issues.
What is SAP GRC?
Simply put, the SAP Governance, Risk, and Compliance (GRC) solution is a ready-made strategy and structure that keeps a business safe and on track. Much like running a city or governing a country, corporate governance for companies defines the principles and agreements by which people live — and provides the controls and support that help achieve overall goals. Risk management involves identifying threats and implementing processes to protect against them. Finally, SAP GRC helps the company comply with applicable regulations, follow proper accounting practices, and act ethically.
Now, let’s look at each sub-area in detail.
Governance. The framework controls all a company's activities and their alignment with company goals. Activities include processes, structures, and policies designed to control and monitor corporate activities. This includes centralized management of privacy requirements, policies, records of processing activities and privacy impact assessments, and security business impact analysis. Using it, you can:
◾ Identify security and privacy risks and create a remediation plan to meet objectives and comply with regulatory requirements.
◾ Deploy and manage maturity assessments with flexible and configurable templates.
◾ Manage security and privacy control evaluations and monitor ongoing compliance.
Risk. A sustained process that addresses risks, mitigates them through controls, and ensures risk control according to policy. This includes risk measurement, assessment, maintenance, monitoring, and identification.
It is vital for businesses to set priorities that ensure risks are adequately addressed. Risk management includes pre-determined action plans and workflows to normalize and automate risk remediation.
Compliance. This area helps ensure that activities within a company are in line with laws and regulations. While governance represents the strategic level, compliance is about adhering to specific rules. It can be industry standards, such as PCI-DSS (Payment Card Industry Data Security Standard), or legal rules, such as the EGDPR (European General Data Protection Regulation) or Sarbanes Oxely Act.
SAP GRC tools make it possible to highlight potential risks, take preventive measures, stay compliant with policies and information, and provide appropriate evaluations for compliance requirements.
Entire processes are created from many individual actions, which can be controlled centrally from the GRC system. The SAP GRC is also well-suited because it can easily integrate into the SAP landscape.
How SAP GRC Helps With Business Security
Enterprises that manage to connect the areas of compliance, risk management, and governance benefit from many advantages.

The goal of SAP GRC is to ensure transparency and security. Transparency applies to the auditor, especially regarding external and internal dangers. Both serve to protect against unwelcome economic and criminal consequences resulting from violations of the law and regulations.
Integrating GRC into an existing SAP system makes it possible to uncover and use the potential synergy effects between governance, risk, and compliance management. The concrete design develops through the various strategies and guidelines in the company-specific internal control system.
However, creating a fully integrated and automated GRC with integrated risk is likely to fail without an organized plan. Here, an approach is recommended in which technical and organizational changes are introduced in step with the technological innovations that support the enterprise’s goals.
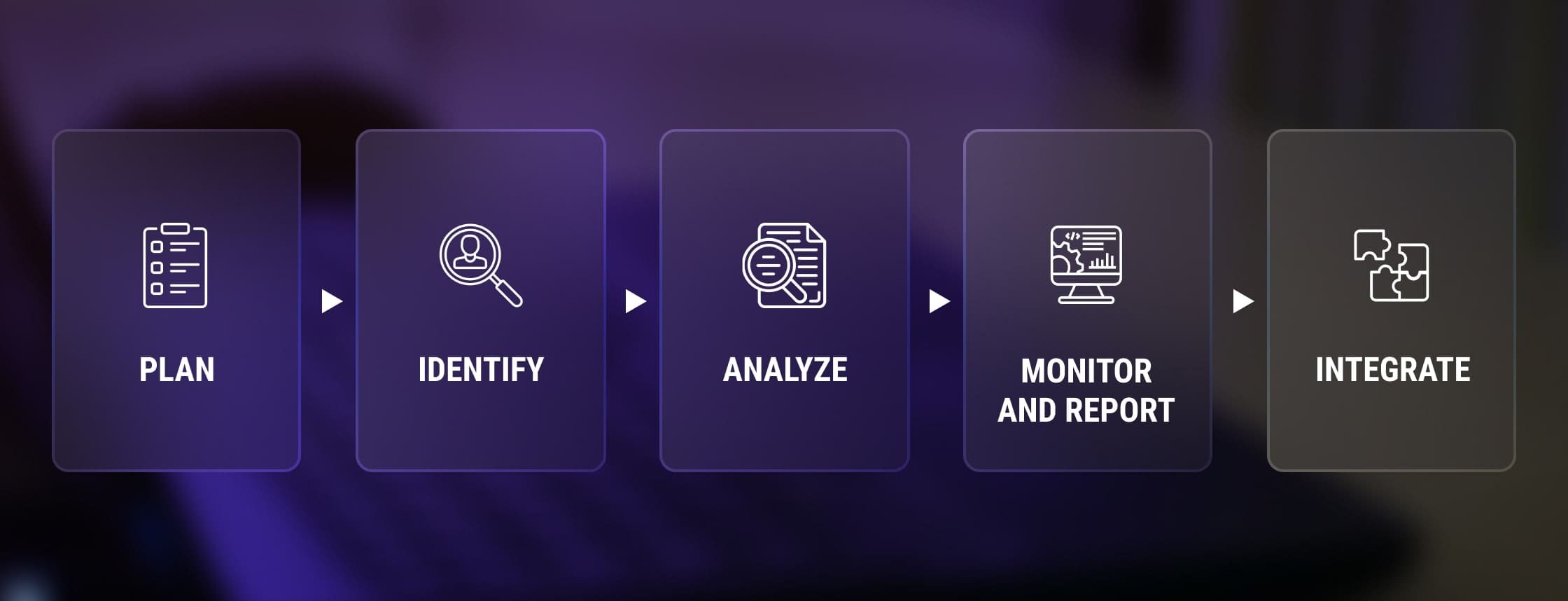
1. Develop a risk mitigation strategy
- Align risk management with strategies and opportunities
- Model and align risks to your organization’s structure
- Create and leverage risk and activity catalogs
- Document risk appetite
- Facilitate risk workshops
2. Identify the key performance indicators
- Use surveys and charting capabilities
- Aggregate by organization category
- Identify drivers and impacts using the application’s risk bow-tie builder
Prioritize using an individualized heat map
3. Analyze the risks assessment criteria
- Determine inherent, residual, and planned residual risk levels
- Examine what-if scenarios
- Identify qualitative and quantitative factors, including velocity
- Automate risk aggregation
4. Set up the monitoring system
- Analytics and reports, including heat maps
- Notifications to risk owners through automated alerts and key risk indicators
- Monitoring response effectiveness
- Assessment of impact on business objectives
5. Ensure smooth software integration into the existing SAP environment
- Document responses
- Assign accountability
- Launch a workflow-driven response with remediation tracking
- Integrate with the SAP Process Control and SAP Audit Management applications
Conclusion
Whether you need specialized functional expertise or just comprehensive security to help you implement the SAP security services, we’ve got an SAP business consultant who can help. Need help with SAP GRC implementation? We have the expertise and knowledge to provide you with top-tier SAP consulting. Reach out for a consultation today!
How useful was this article?
Thanks for your feedback!

-min-Jul-13-2022-10-03-56-83-AM.jpg)

